Fundamentals of Hashing and Encryption
Hashing and encryption are two crucial techniques in cryptography that aim to secure information and maintain its integrity. Both approaches convert raw data into a different format, making it less readable and more secure. Here we’ll explain the fundamental concepts of hashing and encryption, touching on their differences and their primary roles in today’s communication and privacy.
Hashing is a process where an input is transformed into a fixed-size output, known as a hash value, through the use of various hashing algorithms like MD5, SHA, and HMAC. The main purpose of hashing is to guarantee data integrity, meaning that even the smallest change in the input will produce a significantly different hash value. Hashing is usually used in password storage, data verification, and digital signatures. One essential trait of hashing is that it’s a one-way function (hash function), in other words it’s nearly impossible to reverse-engineer the original input from the generated hash.
In the same time encryption also includes the support of encryption algorithms like DES, AES, and RSA to convert plaintext information into ciphertext. Ciphertext is the unreadable output produced by encrypting the plaintext with a specified encryption algorithm and a secret key. Unlike hashing, encryption is a two-way function, meaning that the encrypted data can be decrypted back into its original form using the correct decryption key.
Some of the most popular encryption algorithms are:
- DES (Data Encryption Standard): A widely-used in the past symmetric-key algorithm that uses the same key for encryption as well as decryption. It has been largely replaced by more secure algorithms due to its small key size, making it prone to cracking.
- AES (Advanced Encryption Standard): A symmetric-key algorithm recognized as the industry standard, offering several key sizes while providing excellent encryption and decryption speeds.
- RSA (Rivest-Shamir-Adleman): An asymmetric-key algorithm that uses separate keys for encryption and decryption (public and private keys), making it suitable for secure key exchange and digital signatures.
To summarize, the difference between encryption and hashing lays in the fact that they serve different purposes within the field of cryptography and digital security. While hashing is primarily concerned with ensuring data integrity and theoretically cannot be reversed, encryption focuses on securing data with the feature of being able to decrypt it back into its original form. Both techniques are essential in maintaining the security and privacy of sensitive information.
Hash Functions Vs Encryption Functions
Deterministic Vs Non-Deterministic
Hash functions are of the so called deterministic algorithms, meaning they produce the same output, or hash value, for a given input data every time. This property makes them perfectly suitable for tasks such as verifying the integrity of data or creating unique identifiers. For example, in password storage, a hashing algorithm allows systems to verify a user’s password without storing it in plaintext, as the same password will always produce the same hash value.
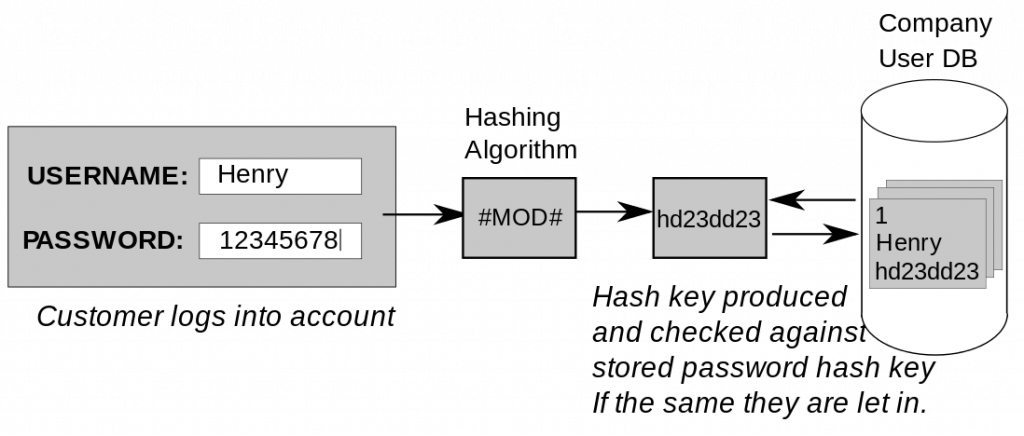
On the other hand, encryption functions can be non-deterministic, especially when using modes that involve randomization, such as Initialization Vectors (IVs) in symmetric encryption of the key. In these cases, the same input (plaintext) may produce different outputs (ciphertext) each time it is encrypted, even if the same encryption key is used. This randomness improves security by making it harder for attackers to deduce the original plaintext through statistical analysis of the ciphertext.
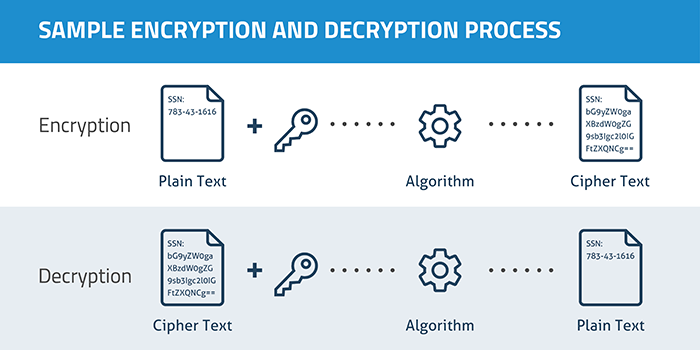
Reversible Vs Irreversible
Encryption functions are reversible, which means that given the correct encryption key, it is possible to decrypt the ciphertext back to its original plaintext. This two-way nature of encryption is fundamental to its purpose of securely transmitting or storing private data without loss of information, allowing authorized parties to access and understand the data when needed.
In contrast, hash functions are designed to be irreversible, making it computationally infeasible to retrieve the original input from the hash value. This one-way property is beneficial when it is necessary to obscure sensitive data, such as password storage or digital signatures. Hashing an input text creates a hash value, while encryption transforms the data into ciphertext. The main goal of hashing is to provide a fixed-size, unique representation of the data, without allowing it to be reconstructed.
In brief, both hash functions and encryption functions serve different purposes in the realm of digital security:
- Hash functions: deterministic, irreversible, suitable for data integrity and obscuring private data
- Encryption functions: can be non-deterministic, reversible, appropriate for secure data transmission and storage of sensitive information
Password Security and Storage
Password Hashing
Password security is essential in today’s digital world. A key aspect of ensuring robust password security is choosing the right method for password storage and how decryption would take place. The preferred method is using password hashing. It is a one-way function that makes it impossible to decrypt a hash and obtain the original plaintext value (password). Hashing algorithm types like MD5 and SHA256 are commonly used for this purpose.
When a user enters their password, the system hashes (converts) it and compares the hashed value against the stored hash in the database. If the hashed values match, that would mean the password is correct and the user is granted access. As hashing is considered infeasible to reverse, it prevents unauthorized users from discovering the original password, even if they manage to access the hash database. It is a fail-safe mechanism for when data leaks occur.
Salting and Its Importance
Salting is another vital aspect of password security. A salt is a random piece of data that is generated for each user and combined with their password before the hashing process. By adding the salt to the password, the resulting hash becomes more unique, even for identical passwords among different users. This enhances the security of the stored passwords. It is just an extra level of security.
Salting makes it more difficult for cybercriminals to use precomputed tables (also known as rainbow tables) to crack hashes and discover the original passwords. When salts are used, attackers must generate new rainbow tables for each salt, which is way less efficient from the attacker’s point of view, making the process more time-consuming and resource-intensive.
All to all, password hashing and salting are crucial for secure password storage. These techniques help maintain the confidentiality and integrity of anyone’s data, reducing the risk of unauthorized access and potential data breaches.
Data Security and Cryptography Techniques
Data security is a vital aspect of digital information, and cryptography plays a key role in achieving it. This section below will focus on understanding the difference between encryption and hashing, and specifically, how these techniques contribute to data security. Cause let’s be honest – that is the whole point of having such techniques available.
Encryption in Transit and at Rest
Encryption is a process that converts plaintext into unreadable ciphertext. It helps keep data secure while it is being transmitted over a network (in transit) or stored in databases, hard drives, or other storage media (at rest). Encryption algorithms use keys to reverse the encryption, rendering the ciphertext back into plaintext. There are two types of encryption: symmetric encryption, which uses a single private key for both encryption and decryption, and asymmetric encryption, which uses separate public and private keys to encrypt data and decrypt the data respectively.
Digital Signatures
Digital signatures are an implementation of asymmetric encryption algorithms that guarantees the integrity, authenticity, and non-repudiation of digital messages or documents. They are created using a private key, while the corresponding public key is used by recipients to verify the signature. By checking the digital signature, a recipient can confirm that the message was indeed sent by the claimed sender and that it has not been tampered with during transit.
Non-Repudiation
Non-repudiation is an essential aspect of cybersecurity, ensuring that a sender cannot deny sending a message or a data transaction. Digital signatures provide non-repudiation by linking the sender’s identity with the encrypted message. If a message is later retrieved and decrypted using the sender’s public key, it guarantees that the message was genuinely sent by the owner of that key pair.
In summary, encryption and hashing are two distinct cryptography techniques used for data security and cybersecurity. Encryption helps protect data in transit and at rest, while digital signatures and non-repudiation ensure the authenticity and integrity of digital messages or transactions. By employing these techniques, businesses and individuals can better safeguard their sensitive information in the digital realm.
Strength and Vulnerabilities of Algorithms
Cryptographic Hashing Strength
Cryptographic hashing algorithms are an essential component of modern digital security. They provide a level of integrity and data verification. Among various hashing algorithms, some widely used ones include SHA-1, SHA-2, CRC32, Tiger, and Whirlpool.
SHA-1 was once a popular choice for its high speed and relative security. However, over time, it has become vulnerable to collision attacks, which significantly compromise its security. As a result, experts now recommend using the more robust SHA-2 family of algorithms, which offers better protection against attacks and improved confidentiality.
Others from the type secure hashing algorithm, like CRC32, Tiger, and Whirlpool, also have their unique strengths and vulnerabilities. For instance, CRC32 is known for its error-detection capabilities but is considered weak from a cryptographic perspective. On the other hand, algorithms such as Tiger and Whirlpool offer higher levels of security but can be slower compared to others.
Encryption Algorithm Strength
Encryption algorithms serve an entirely different purpose than hashing algorithms. They are primarily focused on providing data confidentiality rather than verifying integrity. Some well-known encryption algorithms include Blowfish, RC4, and Two-way functions.
Blowfish is a symmetric-key encryption algorithm that offers robust security through its variable-length private key. It is simple, fast, and widely adopted for applications like file encryption. However, weaknesses in its key schedule may create opportunities for attacks on certain reduced-round variants of the algorithm.
RC4 was once a popular choice for its speed and simplicity, but over time, it has been found vulnerable to various attacks. For example, weaknesses in its private key generation and keystream make it less secure, leading to its deprecation in favor of more modern encryption methods.
Two-way functions are a group of encryption algorithms designed to be both reversible and computationally secure. Examples include RSA and elliptic curve cryptography. These encryption techniques offer stronger security compared to their counterparts but often require more computational resources, making them slower in some instances.
When choosing an encryption algorithm, it is crucial to weigh the balance between performance, security, and application needs. Understanding the strengths and vulnerabilities of different algorithms helps make informed decisions for best protecting sensitive information.
Applications and Best Practices
Key Management
Effective key management is crucial for both encryption and hashing techniques to ensure data security. One common approach to manage keys is using a public key infrastructure (PKI). PKI provides a framework for authentication, data integrity, and privacy by managing the creation, distribution, and revocation of cryptographic keys. It works by implementing a digital certificate to associate a public key with a user’s identity while a trustworthy certificate authority validates the identities1.
Securing Sensitive Information
Encryption is a method to have sensitive information protected by simply converting plaintext data into ciphertext, which can only be reversed or decrypted using the correct encryption key usually known only by whoever created it initially. There are various encryption algorithms available, such as the Advanced Encryption Standard (AES) and Twofish, which offer different levels of security and computational power requirements. Encryption is mainly used to ensure confidentiality, making it an essential tool for protecting data in transit or at rest.
On the other hand, hashing focuses on data integrity by generating a fixed-size hash code from the input data. Unlike encryption, hashing is a one-way function, meaning that it is nearly impossible to reverse-engineer the original data from the hash code. Hashing is often used for password storage and verifying data authenticity, as it allows users to compare the hash codes without exposing the actual plaintext data5.
In summary, both encryption and hashing play critical roles in securing sensitive information. Encryption provides data confidentiality, whereas hashing emphasizes data integrity. By understanding the use cases and best practices of these techniques, organizations, no matter of the size, can implement robust security measures to protect their sensitive data from unauthorized access, data leaks, cyber attacks and tampering.
Challenges and Future of Hashing and Encryption
As technology evolves, the challenges associated with maintaining and improving the security of sensitive information through hashing and encryption systems are constantly increasing. This section will explore some of the emerging technologies, the potential threats and the future landscape of hashing and encryption.
Emerging Technologies
Advancements in computing power, including quantum computers, are making it increasingly possible to break previously secure encryption algorithms and hash function types. These breakthroughs are forcing the industry to continuously develop new cryptographic techniques to stay ahead of potential threats.
In the realm of encryption algorithms, it’s crucial to ensure that any new technologies maintain the highest level of security for sensitive information. One example of this is the advent of quantum-resistant algorithms, which are designed to withstand attacks by quantum computers, making it more difficult for hackers to decrypt private keys and other information.
Collision-Resistant Hashing Algorithms: RIPEMD
Similarly, in the world of common hashing algorithms, new methods are being developed to ensure data integrity checks and to minimize the risk of collisions (instances where two different plaintext inputs generate the same hash output). This is essential in maintaining the security of applications such as hash tables, which rely on unique hash outputs for efficient indexing and retrieving of information in a computer system. One example of a collision-resistant hashing algorithm is RIPEMD, which is used in cryptographic hashing applications where the integrity of a message digest is essential.
Hardware Security Modules (HSMs)
In addition to encryption and hashing algorithm advancements, new technologies are also improving the way data is stored and handled, making it harder for breaches to take place. For example, the use of hardware security modules (HSMs) in combination with encryption and hashing algorithms help secure the sensitive information and private keys within a computer system. This can make it more difficult for hackers to compromise an organization’s security measures.
Despite these advancements, it is essential to remain vigilant and stay informed about emerging technologies, methods, and potential threats. Organizations must continually adapt to and implement new cryptographic techniques and digital encryption measures to keep sensitive information secure and maintain the highest level of data integrity checks and secure message digests.
By embracing innovation, staying up-to-date on advancements in cryptography, and proactively addressing potential challenges and threats, the future of hashing and encryption seems promising in overcoming the ever-changing technological landscape.
